Ajax MotionCam (PhOD) Jeweller
- Product Code: AJX-M-MCIP
- Brand: Ajax
Description

Lightning-fast alarms. Verified.
MotionCam (PhOD) Jeweller has a built-in camera that takes photos once the detector is triggered. It needs just 9 seconds to show the actual situation on the scene. With visual evidence available in Ajax apps, the security company can quickly verify the threat and respond accordingly. Photo verification relieves users of unnecessary anxiety and prevents security companies from false patrol calls. Users can take an on-demand photo with a single tap to monitor their house's state at any time. The detector can also automatically take photos by an alarm of another device in the system, by a specific schedule, and by arming or disarming.
Peace of mind on demand
The detector needs just a few seconds to show the actual situation on the scene and dispel the user's doubts in case of an alarm. It takes a click in the Ajax app to take an on-demand photo. Also, the detector can automatically take photos by schedule, when another detector in the system is triggered, and when someone arms or disarms the system.
HDR for challenging lighting conditions
MotionCam (PhOD) Jeweller captures clear, balanced images using an advanced optical system, a CMOS sensor, and HDR (High Dynamic Range) technology. HDR improves colors and contrast by combining photos with different exposures into one. This prevents images from being too bright or too dark. As a result, photos look more colorful, detailed, and natural — just like we see things in real life.
Privacy first
Detailed event log
The event log records 500 recent events within the system. The data is explicit with the device, time, and event description. On-demand photos are linked to the user who requested them. Photos can be received only by users with the Photo on Demand access. Security companies do not receive the photos.
Strict permission distribution
The Privacy menu in Ajax apps helps accurately adjust access to visual data for users and security company operators: who and when can request a photo, which detector can take on-demand photos, and who can view the received pictures or streams from integrated surveillance cameras.
Encryption and GDPR
Photos are encrypted at every stage of transmission. Only system users can access the virtual Ajax Cloud storage and view photos. While stored, no photos are processed or analyzed. The Ajax Cloud service is hosted on geographically distributed servers that meet the General Data Protection Regulation (GDPR) requirements.
Discover future-proof hardware
No intruder goes unnoticed
PIR sensor
All Ajax motion detectors use PIR sensors by Excelitas Technologies — a field-leading American manufacturer specializing in designing and producing optronic components since 1931. Ajax Systems constantly proves the sensor’s Superior quality at the production stage: we test 100% of manufactured devices. This approach brings the utmost accuracy of intrusion detection.
Special lens
The pattern of the Fresnel lens sections is designed to differentiate between the IR diagrams of a human, animal, and thermal noise. Large lens sections capture radiation at an adult’s head and torso level. Smaller sections make the diagram more detailed. The lens provides the detector with accurate information about the thermal object in the detection zone and the nature of its movement.
Thermal interferences filter
SmartDetect
We processed thousands of thermal patterns caused by humans, animals, and the environment to develop the SmartDetect software algorithm. In armed mode, the detector constantly analyzes the thermal diagram from the PIR sensor, including the IR radiation intensity, thermal spot size, motion speed, time spent in the detection zone, and other parameters. The algorithm identifies false alarm markers instantly and with high accuracy. As a result — the detector accurately responds to human motion without false alarms.
Temperature compensation
Temperature compensation is a software mechanism that maintains the contrast of the thermal diagram even if the ambient temperature is close to the temperature of the human body. With each ambient temperature measurement, the detector corrects the PIR sensor data according to the coefficient table stored in its memory. The detector is effective over the entire operating temperature range.
Sensitivity level
The detector can adapt to the conditions of a particular facility, considering possible thermal interference or pets. The sensitivity setting changes the set of markers by which false alarms are filtered. Low sensitivity makes the detector less likely to respond to an active pet. High sensitivity raises the alarm in case of any motion in the detection zone.
Professional installation
With the correct installation at the height of 2.4 m and lens direction perpendicular to an alleged intrusion path, the detector provides an accurate thermal diagram and pet immunity. It instantly responds to a real threat, minimizing false alarms caused by animals weighing up to 20 kg and below 50 cm in height.
Stable operation with pre-installed batteries
MotionCam (PhOD) Jeweller comes equipped with pre-installed batteries, boasting a remarkable 5-year lifespan. Ajax apps proactively notify both the monitoring company and users of a low battery level a couple of months in advance. The batteries are replaceable, allowing the installer to simply swap them out after five years. Thanks to the batteries, MotionCam (PhOD) Jeweller functions independently of the facility’s power grid.
- Up to 5 years of operation from pre-installed batteries
- Low battery level warning
- Replaceable CR123A batteries
Jeweller | Wings
Unique wireless technologies
MotionCam (PhOD) uses Jeweller and Wings proprietary radio protocols for reliable communication
- Up to 1,700 m of radio communication3 with a hub or range extender
- Encrypted two-way radio communication
- Notifications about jamming and connection loss
- 9 seconds to deliver the first photo
Communication through steel and concrete
Some facilities have thick walls, metal partitions, or sheer distances that affect signal quality. Ajax range extenders are designed to increase the range of a wireless network and deliver stable connection with a hub despite the obstacles. And by choosing the model with an Ethernet cable connector, you get an additional communication channel. А single system can accommodate up to five range extenders.
- Up to 5 range extenders within one system
- Ethernet-equipped model available
System supervision
All Ajax devices perform automatic self-diagnosis and report their states to the hub. Essential parameters, including tamper, communication, power supply, and sensor statuses, are continuously monitored. The Ajax Cloud server controls communication between the hub and Ajax apps, ensuring instant notifications for ARCs, security companies, and users. In case of any malfunction or communication failure, an engineer is informed immediately to provide necessary services.
- Automatic device self-diagnosis with status report
- Regular polling to display the current device state on apps
- Instant maintenance notifications
Effortless installation and setup
Sabotage resistance
Tamper alarm
The enclosure has a tamper button, which notifies the security company and users once the device is dismantled from the mount.

Data encryption
All data the system stores and transmits is protected by a block cipher with a dynamic key. Encryption makes it extremely difficult to reprogram the device, replace or steal the data.

Data-rich notifications
The Ajax system instantly notifies about alarms and events with informative notifications: security companies and users know exactly which device triggered, when and where it happened.

Device authentication against spoofing
The hub checks the device's unique parameters for authentication during each communication session. If any parameter fails the check, the hub ignores device commands.

Regular polling
The device regularly exchanges data with the hub. The system controls each device state and reports if there is a malfunction or connection loss.
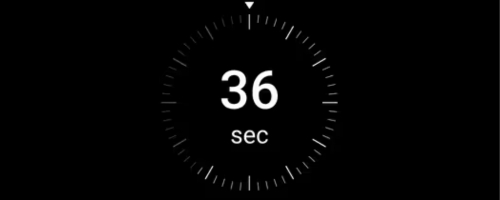
Communication failure detection
The device regularly exchanges data with the hub. With maximum ping interval settings available (3 data packages once in 12 seconds), it takes only 36 seconds to identify communication loss and notify the security company and users about the incident.

















